I keep getting messages that someone tried to login and failed. Hack Instagram Account By Sending.
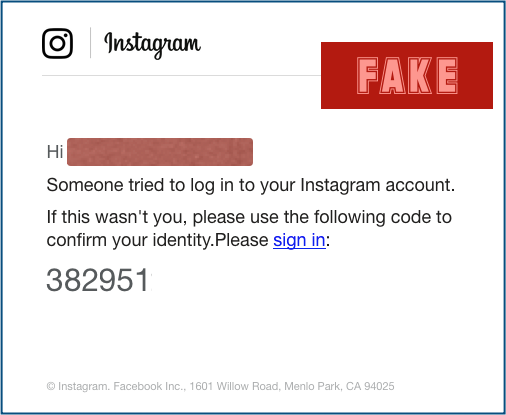 Instagram Phishing Emails Use Fake Login Warning Baits
Instagram Phishing Emails Use Fake Login Warning Baits
The attacks spoofing Mailgun and SendGrid see figures 1-4 below which were first discovered in early June.
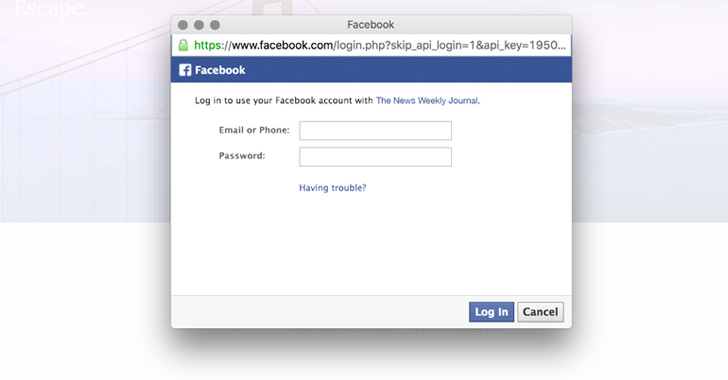
Fake login attack. From that malicious link scammers will send you to a malware download or a faked login pagecomplete with a familiar logo and spoofed URLfor the purpose of harvesting your username and password. In this tutorial Ill teach you to step by step explanation of. This gives additional authenticity to the process as captchas are mistakenly believed to only belong to authentic web pages when in fact they are simply an added security layer to prevent bots from.
In late 2006 a computer worm unleashed on MySpace altered links to direct users to fake websites made to steal login credentials. If you follow our blog then you may have read one of our many articles this year about the growing cyber threat of fake login pages. I am a generally happy Sucuri user on a number of sites.
Principles detailed here are simple but strongly related to SQL injection in string parameters. Login bypass is without a doubt one of the most popular SQL injection techniques. These nefarious yet often highly realistic looking pages are now a common tactic deployed by attackers seeking to obtain a persons login credentials to a legitimate website such as a bank email client or social media site among many other popular services.
Contribute to XeusHackFake-Login-Page development by creating an account on GitHub. What is a phishing attack. The hospitality sector was the hardest hit with an 82 malicious login rate.
The threat of botnets increased in 2018 with over 40 of automated login attempts to websites being malicious. In this phishing attack method attackers simply create a clone website of any website like Instagram Facebook Gmail Twitter etc. If Victim takes login in this fake page then his email and password will be saved in your shadowave account using which you can login to that Victims Instagram account.
This article presents different ways an attacker can use to defeat a login form. There are many more ways a spoofing attack can play out. In this tutorial Im going to show you how to create a Phishing page and also How to do Phishing Attack.
In phishing an attacker creates a look alike page of any popular website and sends it to the victim. The growing attacks on IoT Internet of Things devices make the consequences of phishing more severe. Creating fake login page is called as phishing.
Fake Login Attack Continues Even With Directory Protectee. The success ratio analysis also relies on the long-term web account login failuresuccess rate. Phishing is a type of social engineering attack often used to steal user data including login credentials and credit card numbers.
IRONSCALES researchers have identified a trending fake login attack spoofing two leading email delivery service providers Mailgun and SendGridThis phishing attack was discovered just weeks after our researchers disclosed a massive phishing attack targeting PBX voicemail integrations. So far they have failed. Antoine Vincent Jebara co-founder and CEO of password managing software Myki told The Hacker News that his team recently spotted a new phishing attack campaign that even the most vigilant users could fall for Vincent found that cybercriminals are distributing links to blogs and services that prompt visitors to first login using Facebook account to read an exclusive article or purchase a.
SQL Injection Login Bypass. The aspiring phisher will often build and link to a fake website or login page in the malicious communication attempting to trick the victim into credential theft or entering login credentials andor personal compromising information such as proprietary company information banking details social security. For cybercriminals sending a phishing email is just the first step of the process.
Some of these attacks add another layer to make them even more believable. When the victim enters his login info the attacker gets the credentials. Resolved ThirstyJon thirstyjon 1 year 9 months ago.
Captcha forms when users first click on a fake login URL see Figure 3. Understanding SQL injection attacks against login form. A fake login page for use in a phishing attack.
The fake accounts are typically created some days or weeks before the main attack and may even be actual human logins registering with fake data and a real working email address. It occurs when an attacker masquerading as a trusted entity dupes a victim into opening an email instant message or text message. Experiments have shown a success rate of more than 70 for phishing attacks on social networks.
In all of them fraudsters rely on the naiveté of their victims.
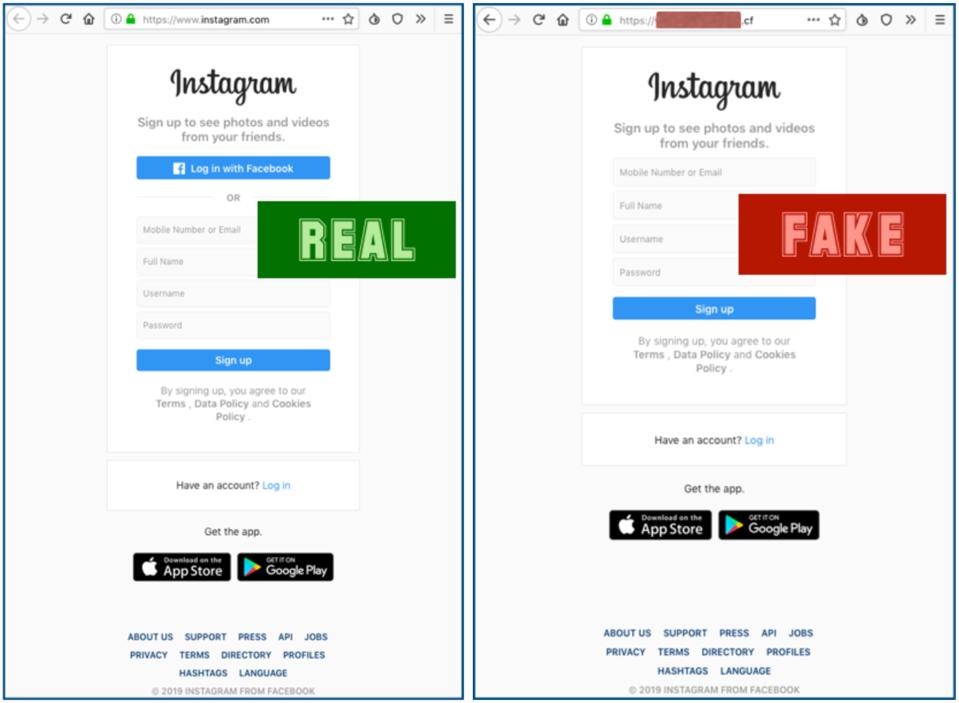 Instagram Security Warning Millions At Risk From Believable New Phishing Attack
Instagram Security Warning Millions At Risk From Believable New Phishing Attack
Github Wifiphisher Wifiphisher The Rogue Access Point Framework
 Fake Login Attack Spoof Two Leading Email Delivery Service Providers
Fake Login Attack Spoof Two Leading Email Delivery Service Providers
 Hack Free Site Facebook Phishing Attack
Hack Free Site Facebook Phishing Attack

 Fake Login Attack Spoof Two Leading Email Delivery Service Providers
Fake Login Attack Spoof Two Leading Email Delivery Service Providers
 Social Engineering Campaign Evades Logo Detection Ironscales
Social Engineering Campaign Evades Logo Detection Ironscales
 Fake Login Pages On Google Translate Used To Carry Out Phishing Attacks Latest Hacking News
Fake Login Pages On Google Translate Used To Carry Out Phishing Attacks Latest Hacking News
 Warning New Phishing Attack That Even Most Vigilant Users Could Fall For
Warning New Phishing Attack That Even Most Vigilant Users Could Fall For
 Phishing Attack Exploiting Office 365 Branding On Fake Login Page
Phishing Attack Exploiting Office 365 Branding On Fake Login Page
 How To Make A Fake Login Page Of Instagram Facebook Twitter And Stoling Passwords Goldenhacking
How To Make A Fake Login Page Of Instagram Facebook Twitter And Stoling Passwords Goldenhacking
 Fake Login Attack Spoof Two Leading Email Delivery Service Providers
Fake Login Attack Spoof Two Leading Email Delivery Service Providers


No comments:
Post a Comment