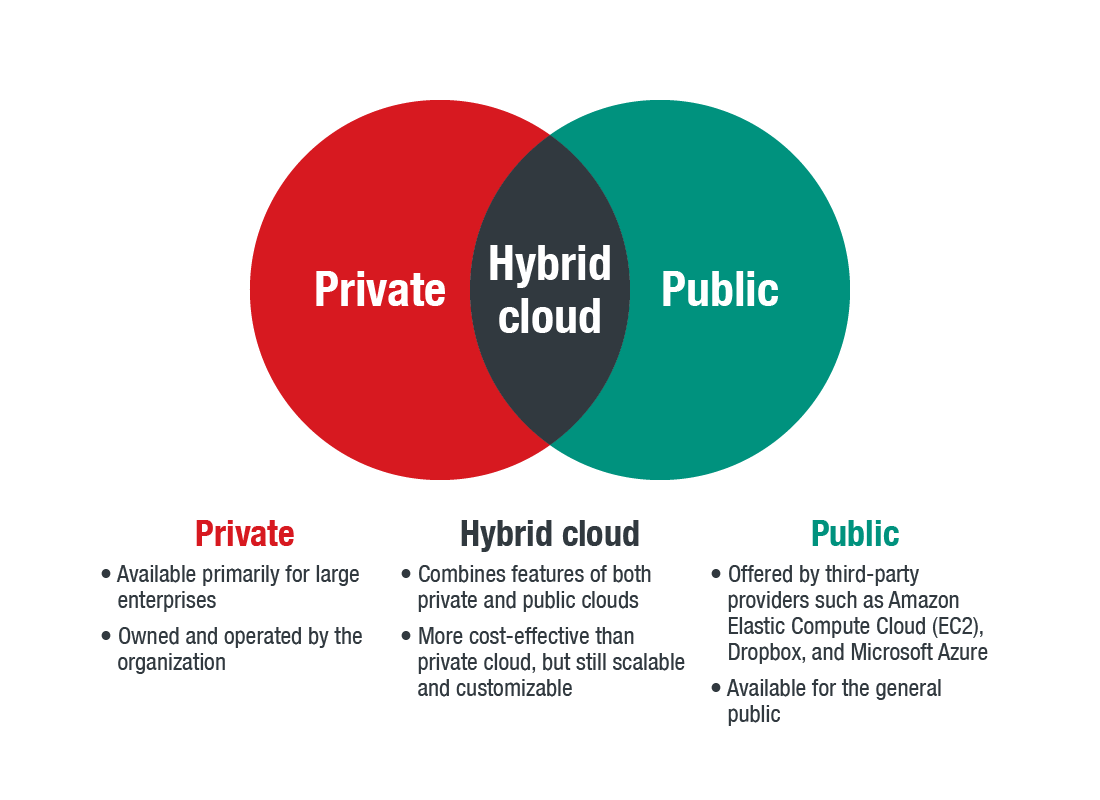
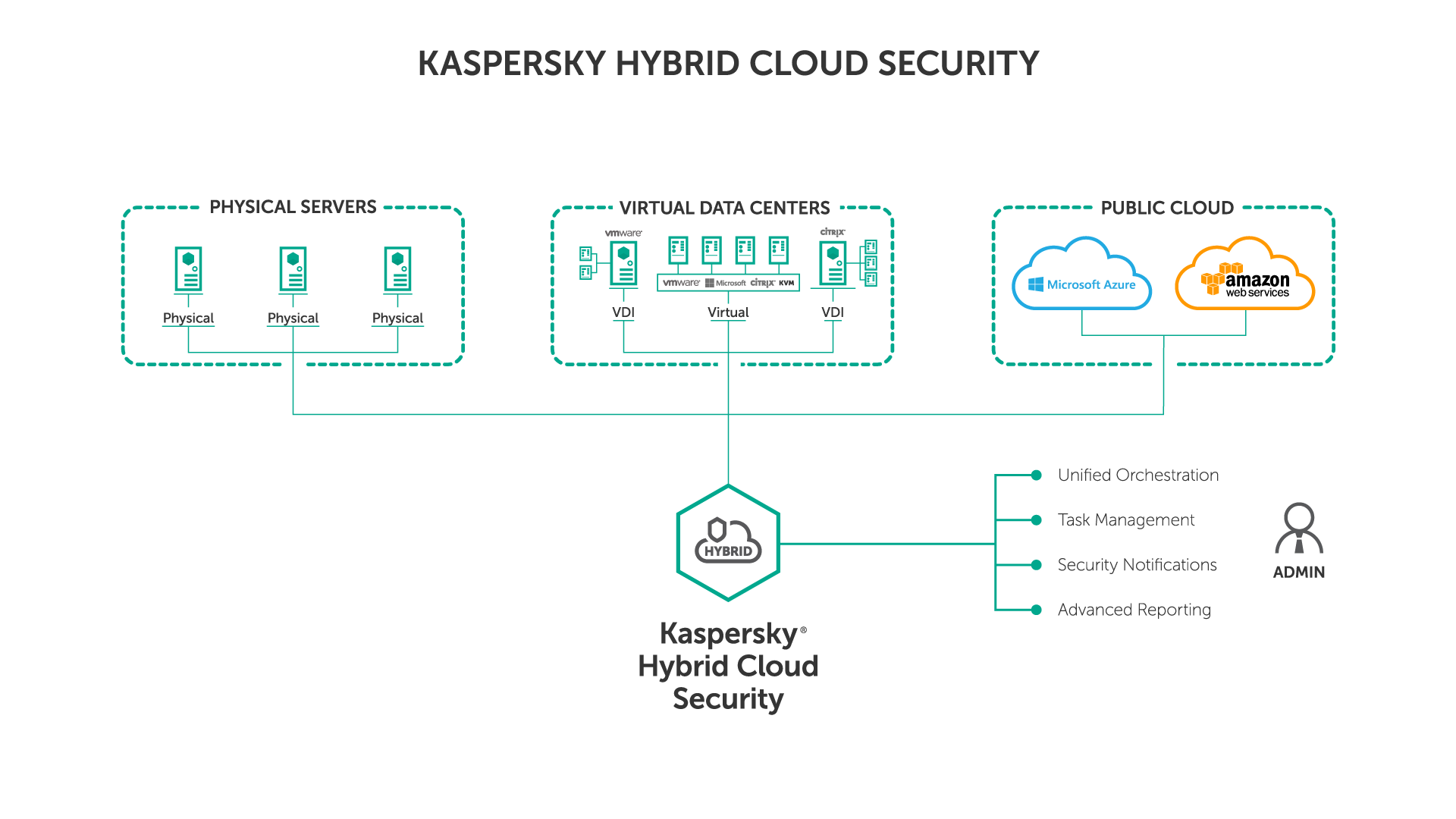
Compare courses from top universities and online platforms for free. Carnegie Mellon University is home CyLab a security and privacy institute that supports research and education in cyber security.
 20 Best Online Schools For Cyber Security Best Choice Schools
20 Best Online Schools For Cyber Security Best Choice Schools
Subbalakshmi Lakshmipathy College of Science Madurai.

Top colleges for cyber security. 19750 BSc - First Year Fees Cyber Security. 78090 MSc - First Year Fees Cyber Security. List of 55 Top Cyber Security Colleges.
Together we can make networks devices and applications more secure. Its a large public four. 21 rows Ferris State University offers 5 Cyber Security degree programs.
As a result Anderson is well on its way to becoming one of the best cyber security schools for students who want to work in government or public administration. The universitys Cyber Security Engineering Laboratory opened in October 2017 and it state of the art. It provides students with real life experience in order to enhance and better.
In Cybersecurity tie 2 in Computer Science tie Carnegie Mellon University a private institution in Pittsburgh is the countrys only school founded by industrialist and philanthropist Andrew. Together we can make networks devices and applications more secure. Ajeenkya DY Patil University School of Information Technology.
Ansal University Gurgaon Haryana. See full list of best cybersecurity schools offering quality degree programs. Ad Explore new cybersecurity trends technologies and approaches.
Ad Free comparison tool for finding Data Analysis courses online. Undergraduate cyber security programs can be found at many top schools and colleges across the country including the University of Southern California Iowa State University and DePaul University. Bellevue University offers both Bachelors and Masters degree programs in Cybersecurity.
USA the UK Estonia have most of the best cybersecurity schools in the world. Ambedkar Institute of Advanced Communication Technologies and Research. Ad Explore new cybersecurity trends technologies and approaches.
Take a look at some of the colleges offering undergraduate and postgraduate level degree courses in cyber security. Situated in Bellevue Nebraska Bellevue Universitys Center for Cybersecurity Education is designated as a National Center of Academic Excellence in Information AssuranceCybersecurity by the NSADHS. Compare courses from top universities and online platforms for free.
The institute coordinates with. Ad Free comparison tool for finding Data Analysis courses online.