Each data masking job can be saved as a task that you can automate or schedule locally on your machine or remotely on your server. What are Data Masking Technologies.
 Data Masking What It Is How It Works Types Best Practices
Data Masking What It Is How It Works Types Best Practices
Keep all your data in Salesforce.

Data masking tools. DATPROF Data Masking Tool. The integrity of the database is preserved assuring the continuity of the applications. Microsoft SQL Server Data Masking T-Query Windows Linux Mac cloud.
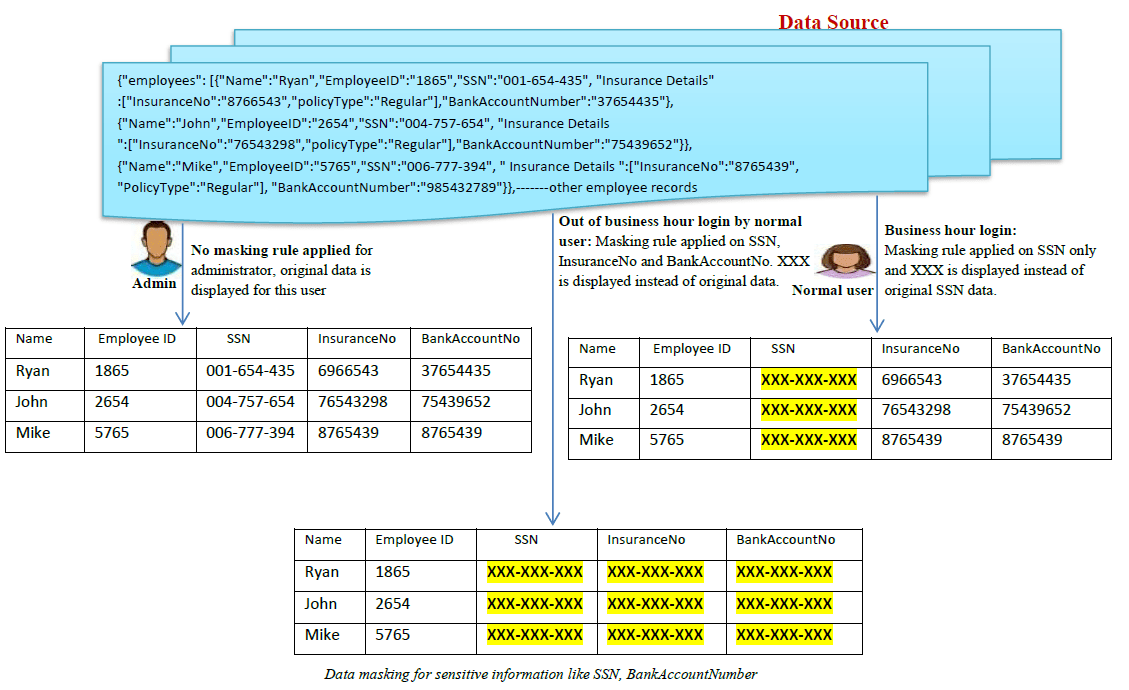
Data masking tools may be used during application development or testing where apps require data input from an end-user. Not masked Null out Exclude field. Microsoft SQL Server Data Masking.
Informatica Persistent Data Masking. IBM INFO SPHERE Optim Data Privacy. Why use data masking.
Centralized management of masking policy audit trail. Data Masking Tools eliminate complex data with false data. The average cost of a data breach was 4 million in 2019.
Delphix is a fast as well as secure data masking tool for masking data across the company. It creates a reliable data masking rule across the industry with a single audit track. Therefore here we have some of the latest data masking solutions or tools which are used to perform.
Simplify your implementation and reduce maintenance costs with a 100 native approach. Information Persistent Data Masking. It delivers enterprise scalability toughness and integrity to a large volume of databases.
It is mostly used by corporate and government IT bodies for masking sensitive data within the flat files databases and other data storage systems. Customizable field-level static data masking Obfuscate each field value type with the right masking method All types. It searches for CSI PI PII PHI PAN and other sensitive information.
Data Masking Tools are protecting tools that avoid any misuse of complex information. Data masking tools may be used during application development or testing where apps require data input from an end-user. These technologies enable organizations to operationally minimize the footprint and propagation of sensitive data or its view without extensive custom development.
They may be used throughout application development or testing where end-user inputs the data. Data masking provides a way to limit the use of private data while enabling business to test their systems with data that is as close to real data as possible. Oracle SQL Server PostgreSQL IBM DB2 EDB Postgres MySQL and MariaDB.
Informatica Persistent Data Masking is an accessible data masking tool that helps an IT organization to access and manage their most complex data. The market for data masking tools regroups offerings designed to desensitize data to protect it against confidentiality or privacy abuse. FieldShield by IRI is a data masking tool.
Automatic Discovery of Sensitive Data and Relationships. The Delphix Masking Engine is combined. IRI Field Shield Structured Data Masking Oracle Data Masking and Subsetting.
It may also be used for instance in a call center where personal data is masked from the call center operative. Data Mask keeps your data inside Salesforce which means no external code API calls or external integrations. Data masking tools generally provide the following features and capabilities.
It comes up with encoded rules for HIPAA PCI DSS and the SOX. GDPR synchronization template Synthetic test data TDM CISO ERD Runtime API Deterministic masking. Data masking is sometimes described as data obfuscation and is related to data encryption and tokenization.
These Extract Transform Load ETL tools may be able to transform or otherwise obfuscate data from point A to point B--but nevertheless require a significant amount of time and infrastructure to do so. DATPROF Data Masking tool. A range of masking techniques available on-demand.
Some data masking tools have tried to tackle the problem of masking large volumes of data. Oracle Data Masking and Subsetting enables entire copies or subsets of application data to be extracted from the database obfuscated and shared with partners inside and outside of the business.