Risk analysis is the primary implementation specification of the first standard in the rule. Risk analysis is a required implementation specification under the Security Management Process standard of the Administrative Safeguards portion of the HIPAA Security Rule as per Section 164308 a 1.
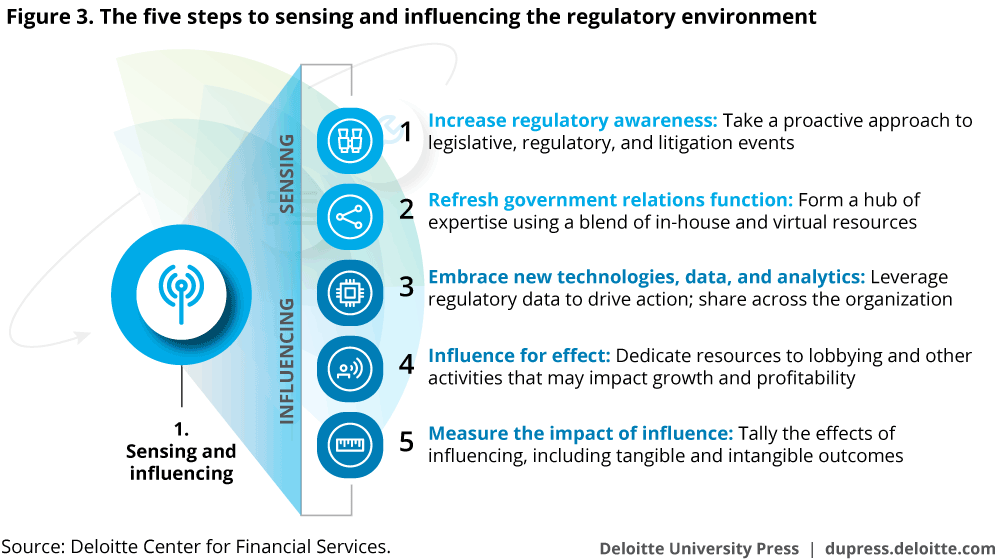 Regulatory And Compliance Risk At Investment Management Firms Deloitte Insights
Regulatory And Compliance Risk At Investment Management Firms Deloitte Insights
A foundational step lies in the US administrations re-engagement with the JCPOA and Irans return to compliance.

The first step toward security rule compliance is. It is perfectly positioned. Being compliant with the HIPAA Security Rule features three main pillars administrative physical and technical safeguards. Several steps can be followed by medical practices to ensure compliance to HIPAA standards.
The literature contains many guidelines for developing and implementing security policies to assist in reaching compliance. In its guidance HHS touts the Risk Analysis as the first step in identifying and complying with the HIPAA Security Rule. The reason for this is the information gathered in completing the Risk Analysis can be used for completing other HIPAA mandated security tasks such as designing an appropriate personnel screening process.
Risk assessment involves analyzing the risks that your systems face daily. Risk Analysis is often regarded as the first step towards HIPAA compliance. A JCPOA plus process must lengthen and strengthen the deal.
Risk analysis is a required implementation specification under the Security Management Process standard of the Administrative Safeguards portion of the HIPAA Security Rule as per Section 164308 a 1. Risk Analysis is often regarded as the first step towards HIPAA compliance. The Security Officer can be an individual or an external organization that leads Security Rule efforts and is responsible for ongoing security management within the organiza-tion.
The Security Rule requires appropriate administrative physical and technical safeguards to ensure the confidentiality integrity and security of electronic. Run a complete risk assessment of the medical practice Some medical practices adopted electronic health recording systems before there were clear guidelines on what these systems should contain. The first step toward Security Rule compliance requires the assignment of security responsibility a Security Officer.
Have a schedule in place with a firm time frame to allow for the old computers to be put back in place should any part of the refresh fail. Enlist the users to back up their own data and restore it thus removing this point of concern and easing the refresh time constraints. The Security Rule essentially ensures that PHI will only be accessible to those who should have access.
The first step in HIPAA compliance is defined within the Security Rule. First the risk of disclosure to unauthorized parties is small in the closed environment. Assess your current security taking special note of any risks and gaps.
Covered entities will benefit from an effective Risk Analysis and Risk. Covered entities will benefit from an effective Risk Analysis and Risk. Under the administrative guidelines businesses handling PHI need to establish a risk assessment plan followed by a risk management plan.
Second encrypting data is costly. The HIPAA Security Rule establishes national standards to protect individuals electronic personal health information that is created received used or maintained by a covered entity. An organizations first step toward the secure information path is a comprehensive and structured information classification process 6 Once a security process plan or policy is in place it must be implemented maintained and evaluated.
In order to ensure youre complying with the security rule take this step-by-step approach. But recommitting to the JCPOA cannot be an end in itself. Develop a plan to implement measures to eliminate the risks and gaps.
All determination of reasonable and appropriate safeguards must flow from. Now is the time to act.