The First Step in Information Security Compliance Behavior. Identify all of its key components including individual servers the networking infrastructure that connects those servers and the software running on them.
 Jual Buku Network Security First Step Kota Bekasi Tb Buku Lengkap Tokopedia
Jual Buku Network Security First Step Kota Bekasi Tb Buku Lengkap Tokopedia
Classification safeguarding dissemination declassification and destruction The unauthorized disclosure of Confidential information could reasonably be expected to cause __________ to our national security.

What is the first step in information security. The first step in an effective information security framework is to understand what exactly your organization is trying to protect. Implementation of those security controls Step 4. First Step to Managing Information Security.
What are the steps of the information security program life cycle. Communicate with all affected parties d. Compare courses from top universities and online platforms for free.
What is the first step in a disaster recovery effort. Categorization of the information system Step 2. RMF provides implementation guidance through a six-step information system life cycle.
The responses of 398 organiza. Perform a Regulatory Review and Landscape Your firm must first perform a regulatory review as all businesses have requirement coming from oversight bodies. The first step after defining the ISMS is to explain it and notify the organisation about the scope and manner of the ISMS operation as well as about how each employee affects information security.
Ad Free comparison tool for finding Data Analysis courses online. Compare courses from top universities and online platforms for free. You can start by thoroughly mapping out your network.
Steps to Create an Information Security Plan. To plan a realistic security program that gets approval from management you need to consider how management likes to operate. Ad The faster way to cyber security solutions results you can rely on.
Ad Free comparison tool for finding Data Analysis courses online. Follow the disaster recovery plan DRP c. Respond to the disaster b.
First things first know your organization. Assessing the selected security controls Step 5. Ill describe the steps involved in security management and discuss factors critical to the success of security management.
Ensure that everyone is safe. Discover the newest cyber security options. Ad The faster way to cyber security solutions results you can rely on.
Forbes reports that 70 of firms experienced at least one cybersecurity incident in 2017. Threat and Vulnerability Assessments. You cant protect what you cant see or dont know exists for that matter.
Selection of security controls Step 3. Discover the newest cyber security options. In this study we use the attentional phase of social learning theory to link workplace security-related experiences and observations to employees security awareness.
The first step of the lifecycle is to map your network identify servers and understand what applications are running on them. Determine and evaluate IT assets. The very first thing to do when entering the information security lifecycle is to identify what it is that youre trying to protect.
 Jual Produk Network Security First Step Termurah Dan Terlengkap April 2021 Bukalapak
Jual Produk Network Security First Step Termurah Dan Terlengkap April 2021 Bukalapak
 Jual Buku Network Security First Step Kota Bekasi Tb Buku Lengkap Tokopedia
Jual Buku Network Security First Step Kota Bekasi Tb Buku Lengkap Tokopedia
 It Cyber Security Discovery Lansweeper It Discovery Software
It Cyber Security Discovery Lansweeper It Discovery Software
 1 Importance Of Information Security Youtube
1 Importance Of Information Security Youtube
Education The First Step To Cyber Security New Report Launched Collaborative Solutions For Network Information Security In Education Enisa

 Jual Network Security First Step Ori Kota Bandung Bandung Im Tokopedia
Jual Network Security First Step Ori Kota Bandung Bandung Im Tokopedia
 Pdf The First Step In Improving Security Awareness A Simple Self Assessment Framework
Pdf The First Step In Improving Security Awareness A Simple Self Assessment Framework
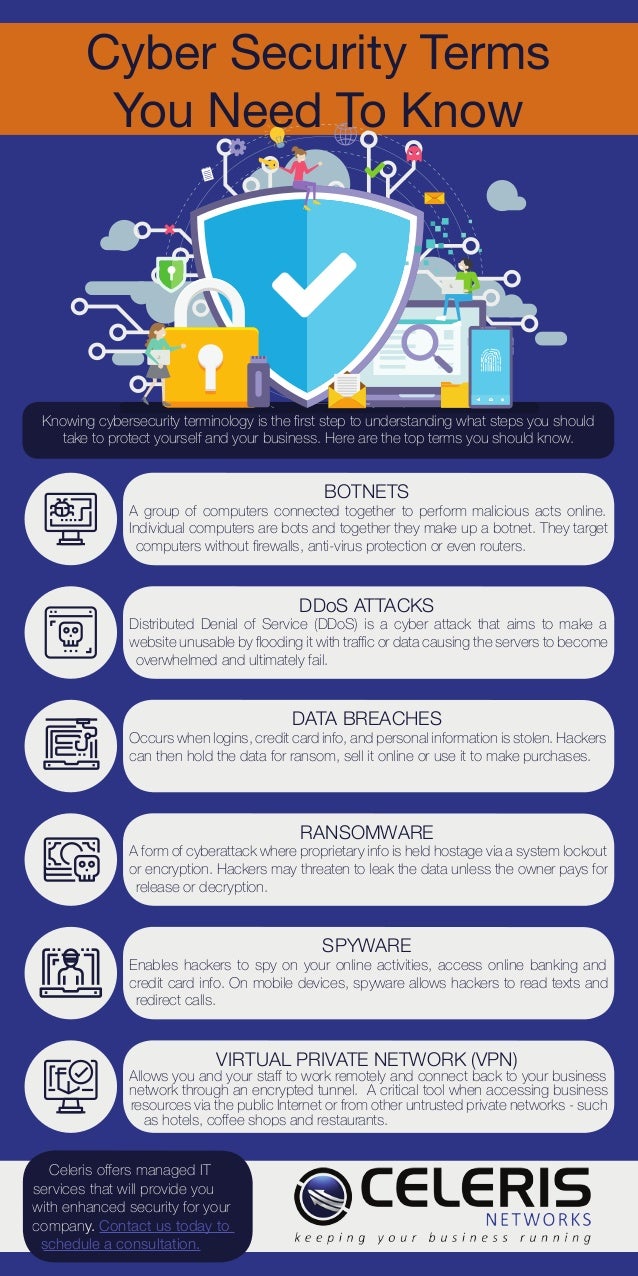 Cyber Security Terms You Should Know To Protect Your Business
Cyber Security Terms You Should Know To Protect Your Business
 Identify And Align Your Information Security Plan With Corporate Strategy
Identify And Align Your Information Security Plan With Corporate Strategy
 Why The Art Of Footprinting Is The First Phrase Used In Information Security By Robert Smith Medium
Why The Art Of Footprinting Is The First Phrase Used In Information Security By Robert Smith Medium
 Network Security First Step Ebook 2nd Thomas Tom Stoddard Donald Buy Online At Pearson
Network Security First Step Ebook 2nd Thomas Tom Stoddard Donald Buy Online At Pearson
 Network Security First Step Di Lapak Sukma Store Bukalapak
Network Security First Step Di Lapak Sukma Store Bukalapak
 Penetration Testing The First Step On Securing Your Business Infrastructure Telkomtelstra
Penetration Testing The First Step On Securing Your Business Infrastructure Telkomtelstra
No comments:
Post a Comment