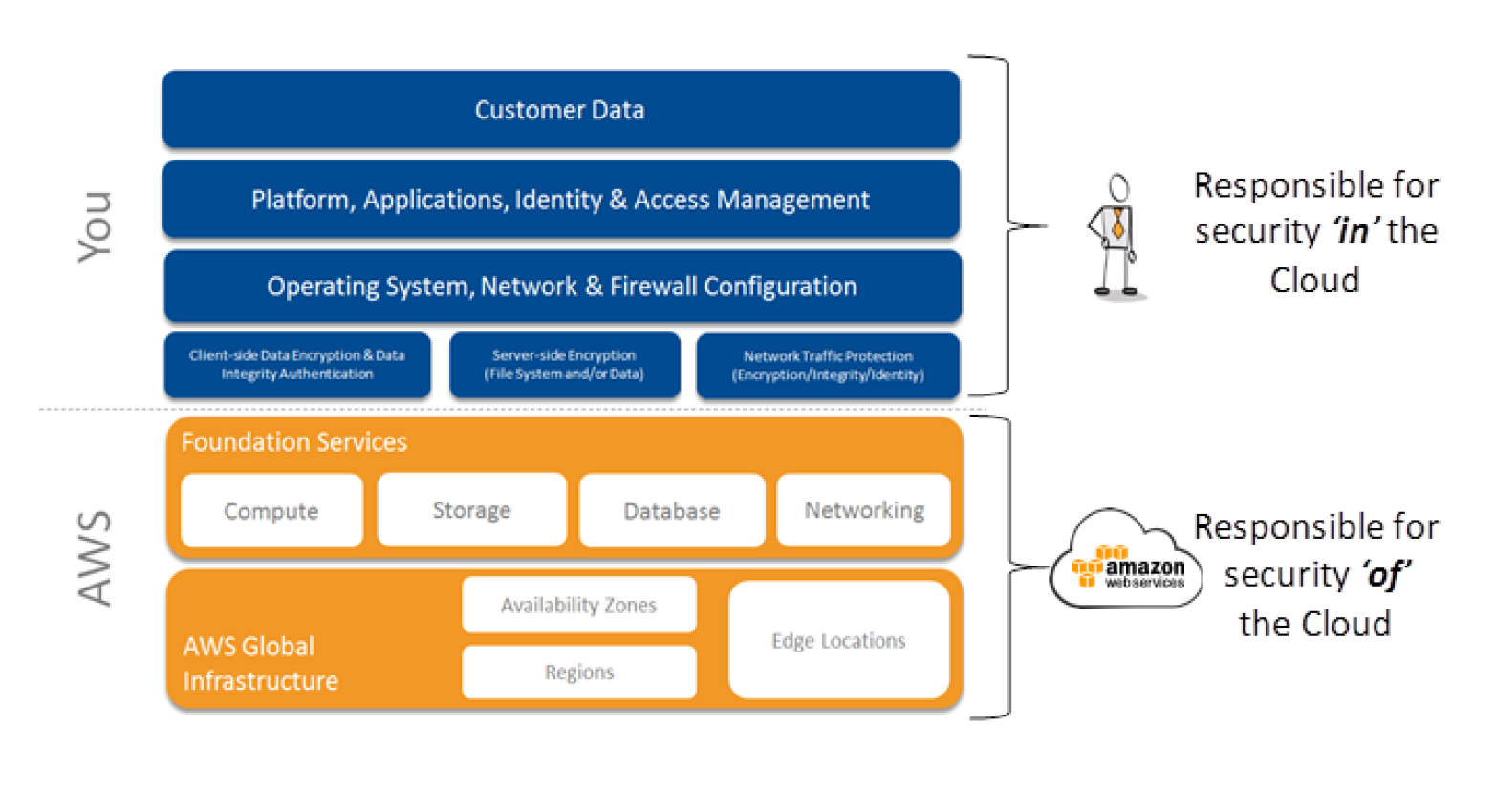
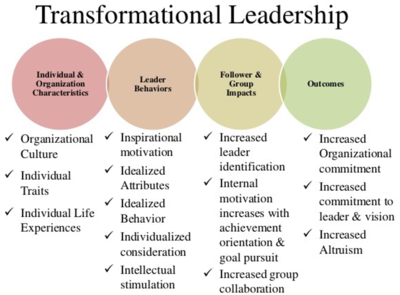
According to Bass these are the hallmarks of a transformational leader that sets them apart from other leadership styles. The simplest terms transformational leadership is a process that changes and transforms individuals Northouse 2001.
 Transformational Leadership Cio Wiki
Transformational Leadership Cio Wiki
Leadership expert James Burns defined transformational leaders as those who seek to change existing thoughts techniques and goals for better results and the greater good.

Who is a transformational leader. A transformational leader is someone who. Perhaps its because they know how to appeal to your why. The Master List of Transformational Leaders.
Transformational leadersare those who stimulate and inspire followers to both achieve extraordinary outcomes and in the process develop their own leadership capacity. They have a charismatic appeal. Transformational leadership is a style of leadership where the leader along with hisher team is able to identify the challenges ahead resources available and build a long-term vision for the team and is constantly engaging and involving the employees to.
Transformational leadership is a leadership theory where a leader works with followers to identify the changes needed create a vision through inspiration and execute the change with a group of highly committed followers. Get Results from 6 Engines at Once. Compare courses from top universities and online platforms for free.
Encourages the motivation and. Transformational leadership may be found at all levels of the organization. Teams departments divisions and organization as a whole.
Ad Search Master Leadership. Compare courses from top universities and online platforms for free. They just dont know how to bore and snore.
It is an integral part of the Full Range Leadership Model. He commands a disruptive company. Ad Free comparison tool for finding Leadership courses online.
This leadership style can increase group morale lead to rapid innovation improve conflict resolution decrease turnover and foster a sense of ownership amongst a team. One characteristic of the great transformational leaders is the ability to inspire. Get Results from 6 Engines at Once.
Such leaders are visionary inspiring daring risk-takers and thoughtful thinkers. Transformational leaders help followers grow and develop into leaders by responding to individual followers needs by empowering them and by aligning the objectives and goals of the individual. But charisma alone is insufficient for changing the way an organization operates.
Ad Search Master Leadership. Transformational leadership is an approach in which a leader inspires and motivates team members to create positive changes within an organization. Burns also described transformational leaders as those who focus on the essential needs of the followers.
In other words transformational leadership is the ability to. Ad Free comparison tool for finding Leadership courses online. In conclusion Jeff Bezos can be considered as a transformational leader the best one in active nowadays.
From Wikipedia the free encyclopedia Transformational leadership is a theory of leadership where a leader works with teams to identify needed change creating a vision to guide the change through inspiration and executing the change in tandem with committed members of a group.